I recently wrapped up a large TMG deployment in support of a new Exchange 2010 resource forest and there were a lot of lessons learned (read: issues that needed to be overcome), so I figured I would try to capture the main ones for the blogosphere.
Part 1 of 3 – Redirection to Legacy Exchange 2003
This article assumes a fairly decent knowledge of both TMG and Exchange. It is not meant to be a detailed step-by-step configuration guide; it only serves to identify the key configuration elements for redirection. All steps should be tested prior to production rollout, usually by editing the hosts file to force traffic to the right IP for testing.
In our original publishing model, ISA or TMG is used to publish the Exchange 2003 FE. Pretty straightforward.
Original Publishing Model
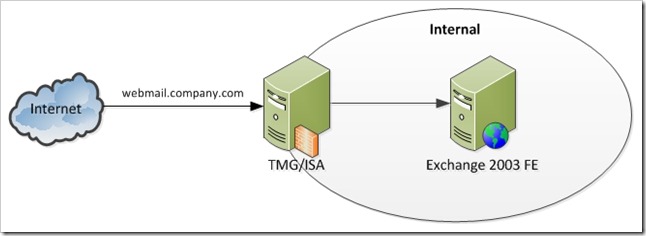
Exchange 2010 in Same Forest as Exchange 2003
In the case of an upgrade/transition to Exchange 2010 (a deployment of Exchange 2010 in the same forest as the legacy Exchange 2003 environment), the Exchange 2010 CAS servers can be configured to hand out a legacy URL for OWA. TMG/ISA is generally used to publish the new Exchange environment under the standard name, and to publish the legacy Exchange environment under the legacy URL.
The goal here has three components:
- Avoid modification of the existing, legacy Exchange environment
- Allow publishing/redirection of OWA for both Exchange 2010 and Exchange 2003 users
- Allow the publishing/redirection with a single sign on
New Publishing Model – Upgrade/Transition in Same Forest

If you were using TMG originally, it is possible to achieve this by deploying a new TMG server/array, or by modifying the publishing rules on your existing deployment.
The steps:
- Install the new public certificate on TMG. The new certificate should have all of the DNS names required by your Exchange 2010 deployment: Autodiscover (autodiscover.company.com), Outlook Anywhere (outlook.company.com), and OWA (webmail.company.com). It should also have the new legacy Exchange URL (legacy.company.com).
- Ensure the certificate on the Exchange 2010 CAS server has the appropriate public name.
- Configure the legacy Exchange URL on the Exchange 2010 CAS (legacy.company.com)
- Create a single Web listener using that certificate, with SSO enable for your domain (.company.com in this example).
- Create and test the appropriate Exchange 2010 publishing rules, using the above listener:
- OWA (for the public name webmail.company.com)
- OA (for the public name outlook.company.com)
- Autodiscover (for the public name autodiscover.company.com)
- Create and test a new Exchange 2003 publishing rule, using the same listener as the Exchange 2010 publishing rules.
- Public name must be legacy.company.com, but the old name (webmail.company.com) must be sent to the Exchange 2003 server because it was not configured for the legacy.company.com name. To do this enter the name that Exchanger 2003 is configured for (webmail.company.com) on the “To” tab of the rule, and uncheck the box for “Forward the original host header instead of the actual one (specified in the Internal site name field)”. I also recommend using the IP address of the Exchange 2003 server to avoid DNS issues with the name.

- Create DNS entries for all new public names to the IP of TMG
- Update existing DNS entries (webmail.company.com) to the IP of TMG
For an Exchange upgrade/transition in the same forest, this should meet the required goals. No changes have been made to the Exchange 2003 environment. All publishing rules use the same listener, so single sign on should be working. All users are initially sent to the Exchange 2010 CAS, but if their mailbox is on Exchange 2003, the Exchange 2010 CAS redirects the user to legacy.company.com, which TMG is now configured to publish to Exchange 2003. The only change to the user experience is that Exchange 2003 users will notice their browser change to legacy.company.com, even though they browsed to webmail.company.com.
Exchange 2010 in a Resource Forest
However, there is a SMALL catch for a resource forest – Exchange 2010 redirection to Exchange 2003 doesn’t work. Also, it is important to remember that in a resource forest, user are logging in to their mailboxes with their AD accounts in the account forest, and the AD accounts in the resource forest are disabled.
In general, the TMG architecture is the same, and with a few minor technical modifications and one migration process modification the same goals can be achieved. An added bonus is that the Exchange 2003 does not have the address changed to legacy.company.com in this model, so in the case that the change in address is unacceptable to the business, these same changes can be applied to a normal upgrade/transition as well.
New Publishing Model – Resource Forest 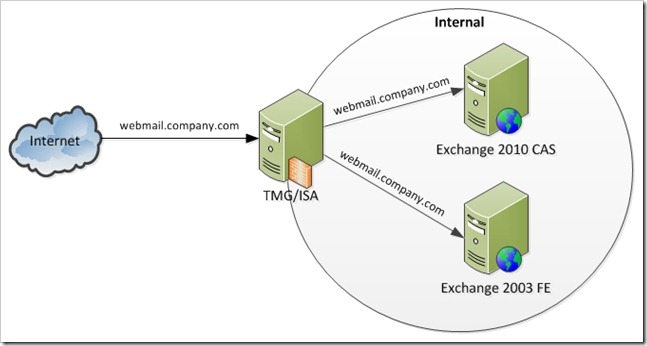
Since Exchange 2010 can’t determine where the user’s mailbox is, we need to configure TMG to handle it.
The TMG configuration detailed in the previous section should be modified as follows:
- Create an AD group that contains the Exchange 2010 migrated users.
- Can be in either in forest, but the accounts in the group must be from the account domain
- Ensure the Exchange 2010 publishing rules are above the Exchange 2003 rule.
- Create a User Set in TMG that contains the newly created group.
- Modify the Exchange 2010 publishing rules to only allow the newly created set (on the “Users” tab).
- Modify the Exchange 2003 publishing rule to allow the traditional public name (webmail.company.com).
With these changes, TMG will only send members of the AD group to Exchange 2010, and all users not in the group will be sent to Exchange 2003. The process change is that you must update the membership of the group as users move to Exchange 2010.
The group is only temporary and is no longer needed once the transition is completed. In that case, remove the Exchange 2003 publishing rule and change the Exchange 2010 rule back to “Authenticated Users”. You can then delete the User Set in TMG and the group in AD.




