Two posts in one day. That might be a new record for me.
I had a 2008 R2 server that wouldn't install Roles properly via PowerShell. When viewing the Roles with Server Manager, it simply said "Error". How useful.
Looking in the event log I found this:
Log Name: Application
Source: Application Error
Date: 12/30/2010 11:18:47 AM
Event ID: 1000
Task Category: (100)
Level: Error
Keywords: Classic
User: N/A
Computer: server.domain.loc
Description:
Faulting application name: TrustedInstaller.exe, version: 6.1.7600.16385, time stamp: 0x4a5bc4b0
Faulting module name: ntdll.dll, version: 6.1.7600.16559, time stamp: 0x4ba9b802
Exception code: 0xc00000fd
Fault offset: 0x0000000000051ae3
Faulting process id: 0x9fc
Faulting application start time: 0x01cba845913dc3d6
Faulting application path: C:\Windows\servicing\TrustedInstaller.exe
Faulting module path: C:\Windows\SYSTEM32\ntdll.dll
Report Id: dc0dfe78-1438-11e0-8fd9-0050568900bb
Event Xml:
<Event xmlns="http://schemas.microsoft.com/win/2004/08/events/event">
<System>
<Provider Name="Application Error" />
<EventID Qualifiers="0">1000</EventID>
<Level>2</Level>
<Task>100</Task>
<Keywords>0x80000000000000</Keywords>
<TimeCreated SystemTime="2010-12-30T17:18:47.000000000Z" />
<EventRecordID>1935</EventRecordID>
<Channel>Application</Channel>
<Computer>server.domain.loc</Computer>
<Security />
</System>
<EventData>
<Data>TrustedInstaller.exe</Data>
<Data>6.1.7600.16385</Data>
<Data>4a5bc4b0</Data>
<Data>ntdll.dll</Data>
<Data>6.1.7600.16559</Data>
<Data>4ba9b802</Data>
<Data>c00000fd</Data>
<Data>0000000000051ae3</Data>
<Data>9fc</Data>
<Data>01cba845913dc3d6</Data>
<Data>C:\Windows\servicing\TrustedInstaller.exe</Data>
<Data>C:\Windows\SYSTEM32\ntdll.dll</Data>
<Data>dc0dfe78-1438-11e0-8fd9-0050568900bb</Data>
</EventData>
</Event>
Generally, this seems to happen when the install process is interrupted (hard stopping a VM or a server losing power during an install). Here are the steps taken to resolve the issue:
- Installed the System Update Readiness Tool for Windows Server 2008 R2. This tools runs when installed, so you don't have to actually run it.
- View the resulting log file (%SYSTEMROOT%\Logs\CBS\CheckSUR.log)
- Found the offending files:
- Change permissions on the %SYSTEMROOT%\servicing\packages directory to allow administrators Modify rights.
- Copy the offending files from a different Server 2008 R2 server to the %SYSTEMROOT%\servicing\packages directory on the problem server.
- Reinstall the offending package (in my case KB2207566).
- Re-run the SUR Tool (by re-installing it).
- View the resulting log file (%SYSTEMROOT%\Logs\CBS\CheckSUR.log)
- Verify the errors have been resolved:
- View Roles with Server Manager.
Summary:
Seconds executed: 131
Found 1 errors
CBS MUM Corrupt Total count: 1Unavailable repair files:
servicing\packages\Package_for_KB2207566_RTM~31bf3856ad364e35~amd64~~6.1.1.0.mum
servicing\packages\Package_for_KB2207566_RTM~31bf3856ad364e35~amd64~~6.1.1.0.cat
Summary:
Seconds executed: 211
No errors detected
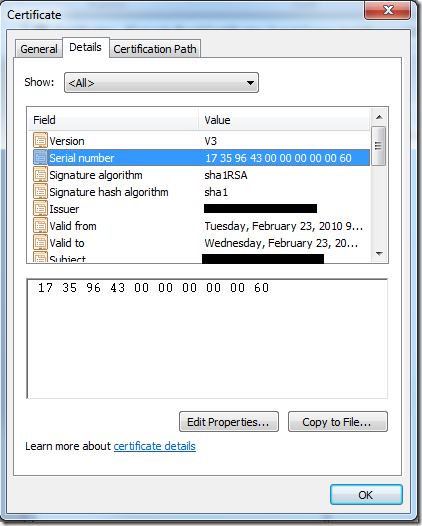

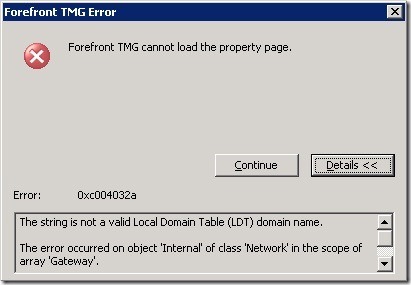 Below is the connection information needed to connect ADSIedit to the AD LDS instance used by TMG:
Below is the connection information needed to connect ADSIedit to the AD LDS instance used by TMG: